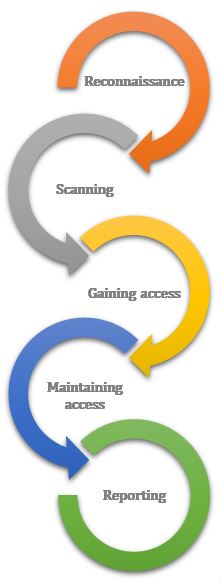
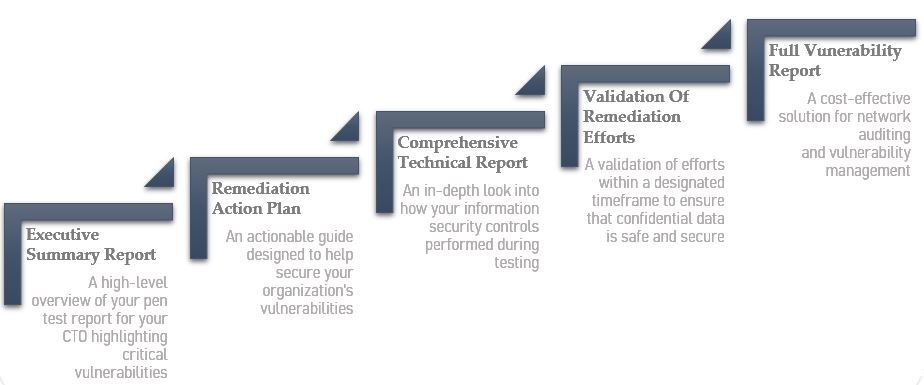
Penetration Testing

GET IN TOUCH
Contact Drivit Solutions today. The best of the best in our teams will get back to you to align with your challenges and address your business requirements.
- info@drivit-solutions.com
- 50 Long Street, Cape Town 8000, South Africa
© Copyright 2021 Drivit Solutions. All Rights Reserved.
×
No WhatsApp Number Found!
WhatsApp us